Pkcs11 Generate New Key Pair
Posted By admin On 12.12.20- Pkcs11 Generate New Key Pair Worksheet
- Pkcs11 Generate New Key Pair Key
- Pkcs11 Generate New Key Pair For Iphone
Proof-of-concept of using an HSM to generate and store key pairs, then using those key pairs to create a CA certificate, client certificate and server certificate for TLS.
Apr 23, 2014 The mechanism generates RSA public/private key pairs with a particular modulus length in bits and public exponent, as specified in the CKAMODULUSBITS and CKAPUBLICEXPONENT attributes of the template for the public key. The mechanism contributes the CKACLASS, CKAKEYTYPE, CKAMODULUS, and CKAPUBLICEXPONENT attributes to the new public key.
You should not be able to read the private key if you generate the key inside the token. You'll need to create a dummy certificate (for example self-signed) and store it with an alias, the keystore model depends on certificates to be usable. 2.1.4 PKCS #1 RSA key pair generation. The PKCS #1 RSA key pair generation mechanism, denoted CKMRSAPKCSKEYPAIRGEN, is a key pair generation mechanism based on the RSA public-key cryptosystem, as defined in PKCS #1. It does not have a parameter. Mar 24, 2019 Name certutil — Manage keys and certificate in both NSS databases and other NSS tokens Synopsis certutil options arguments Description The Certificate Database Tool, certutil, is a command-line utility that can create and modify certificate and key databases. It can specifically list, generate, modify, or delete certificates, create or change the password, generate new public. Proof-of-concept of using an HSM to generate and store key pairs, then using those key pairs to create a CA certificate, client certificate and server certificate for TLS - arsing/openssl-pkcs11-demo. C# (CSharp) Net.Pkcs11Interop.LowLevelAPI81 Pkcs11.CGenerateKeyPair - 2 examples found. These are the top rated real world C# (CSharp) examples of Net.Pkcs11Interop.LowLevelAPI81.Pkcs11.CGenerateKeyPair extracted from open source projects. You can rate examples to help us improve the quality of examples.
Pkcs11 Generate New Key Pair Worksheet
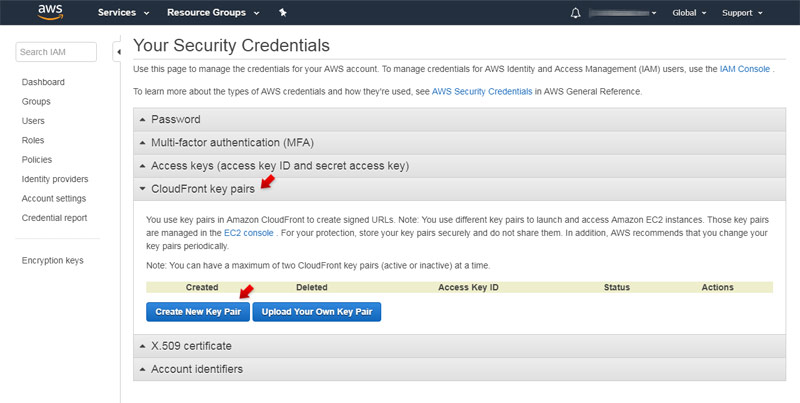
- Linux
- The
openssllibrary softhsm, or any other PKCS#11 library.
Build the project
If using softhsm, clean all existing softhsm slots.
where
~/softhsmis the value ofdirectories.tokendirin/etc/softhsm2.confSet env vars for the PKCS#11 library path, and for the PKCS#11 Spy path if you want to use it.
Initialize three slots.
If you already have an initialized slot in your HSM, set:
TOKENto the token label of the slotUSER_PINto the user PIN of the slotLABEL_{1,2,3}to the values of the object labels that will be used for the three generated key pairs.
Otherwise, initialize them here:
For softhsm, use
softhsm2-utilorpkcs11-tool. Eg:For TPM 2.0 TPMs, use
tpm2_ptoolor any other tool that uses TSS. Eg:
Generate a key pair in each of the two slots.
Possible values for
--typeare listed in the output ofcargo run -- generate-key-pair --helpEach invocation of
generate-key-pairwill print the public key parameters of the newly generated key - modulus and exponent for RSA, curve name and point for EC.Verify the key pairs.
This should print the same key parameters that
generate-key-pairinvocations in the previous step did.Generate certificates using the key pairs /accurate-5-enterprise-key-generator.html.
This uses the first key pair to generate a CA cert (self-signed), the second key pair to generate a server cert (signed by the CA cert), and the third key pair to generate a client cert (also signed by the CA cert).
Start a webserver using the server cert.
The web server runs on port 8443 by default. Use
--portto use a different value.Verify the cert served by the web server.
This should show the cert chain and have no errors (apart from a verification error because the CA cert is untrusted).
This should successfully show
curlcompleting a TLS handshake and receivingHello, world!from the web server.Use a webclient using the client cert for TLS client auth to connect to the webserver.
This should successfully show the client completing a TLS handshake and receiving
Hello, world!from the web server. The client will print the cert chain it received from the server. The server will also print the client cert chain it received from the client.
TPM 2.0 hardware currently does not have a fully-functional PKCS#11 implementation. There is tpm2-pkcs11 but it is not yet feature-complete, and does not work on all hardware.
Pkcs11 Generate New Key Pair Key
Here are some notes of how to use this demo with a TPM:
Your hardware may not work with the latest version of
tpm2-pkcs11, so you may need a specific older version. You may also need specific older versions oftpm2-abrmd,tpm2-tssandtpm2-tools. Consult your hardware manufacturer.Make sure to initialize the
tpm2-pkcs11store first:If using a custom store path (
--path <>), make sure the path is writable by your user.tpm2-pkcs11only supports RSA 2048-bit keys and ECDSA P-256 keys.
Pkcs11 Generate New Key Pair For Iphone
MIT